Laptop monitoring has officially become a key tech solution for businesses tackling the intricacies of modern work environments. With growing remote and hybrid work models being adopted by organizations, there is unprecedented demand for employee monitoring systems. Laptop Monitoring is a category of surveillance that tracks aspects such as employee activity, productivity, and security in distributed workforces.
Laptop monitoring isn’t just surveillance; it’s a solution for workforce management, specifically to enable organizations to ensure productivity and security of sensitive data. Companies are using these systems for insights into staff working patterns, as well as ensuring security, compliance, and the level of efficacy.
However, installing a laptop monitoring system comes with serious legal and ethical issues that organizations need to be aware of and tread carefully. The safety and legality of any monitoring comes down to whether it is intrusive – monitoring needs to be communicated to employees to ensure privacy is respected.
Modern laptop monitoring comes with advanced capabilities that provide employers with information about employee activity, information on applications used, productivity measures, and analytics, rather than just basic time-tracking. With the nature of work ever changing, employers and employees need to understand the significance, effectiveness, and best practices for monitoring.
What is Laptop Monitoring?
Laptop monitoring is the process of systematically observing and recording the activities of employees on laptops issued by the employer, or on laptops owned privately but used for the work of the company. This type of monitoring can involve one or more different forms of surveillance and is performed using special software that can continuously monitor different aspects of a computer’s usage, and can provide the employer with valuable information about the amount of time that is used at work and time spent on non-work activities.
Laptop monitoring is all about surveilling employees using the various types of techniques involved to supervise, record the actions of the employee to truly get a snapshot picture of employee productivity, regarding how employees conduct their work. The different types of monitoring include the measurement of Internet usage behavior, including the recording of the internet websites employees visit, along with the recorded time spent on either, with an actual addition if the material is work-related, or personal. Application Activity Usage is another dimension of monitoring that keeps formal logs of the employee’s applications that are utilized within the employer’s time frame, measuring the frequency that the applications are accessed and the measure of the actual work-related applications are engaged.
Keystroke logging, or keylogging, is one of the more extreme forms of laptop monitoring that records every character typed on the keys of the keyboard. Employers can monitor written communications such as emails, capture document reports, and perhaps even infer any security threats through suspicious behavior of key typing. Screen recordings take snapshots of the employee’s monitor at preset intervals, to gain visual reports and visual proof of the work of the employee, and take stock of the productivity of the employee by watching their pattern of usage behavior.
Today’s laptop monitoring systems also feature advanced capabilities like webcam monitoring, microphone recording, and GPS location tracking for mobile devices. These systems can monitor file transfers, USB device usage, and even printing activity to provide a complete audit trail of employees’ activities. Cloud-based laptop monitoring systems can even allow for real-time monitoring and remote data access for employee activity, which is particularly important for managers of distributed teams.
Laptop monitoring solutions have become so sophisticated that organizations have fine-grained control of what activities are monitored, allowing them to design a monitoring strategy best suited to their business and compliance objectives.
Why Do Companies Use Laptop Monitoring Software?
Organizations may have strategic reasons for implementing laptop monitoring systems; however, production tracking is likely the most prominent motivation. Laptop monitoring facilitates objective observation of employees’ work patterns (hours of peak productivity) and the applications they use most often, as well as how they allocate time across those applications. By accumulating and analyzing this data, a business can optimize workflows, redistribute workloads, or identify employees who, through a lack of monitoring, may need supplemental training. The productivity metrics can provide sufficient data to make informed decisions around the allocation of resources for performance management.
Another important reason for laptop-monitoring implementations can be for insider threat prevention. Organizations are at risk of malicious insiders who could either steal sensitive data, sabotage systems, or commit fraud. Many laptop-monitoring technologies can discover aberrant behaviors, unauthorized access attempts, or unauthorized data transfers, which can be indications of a possible breach. Laptop-monitoring systems monitor communication channels, keep track of files downloaded, and also unnecessary activities that are not in line with usage baselines. If an indication of possible malicious insider activity occurs, an organization can possibly intervene before there is a costly security breach with laptop monitoring.
Regulatory compliance is a reason that drives many organizations to implement laptop monitoring systems, especially those businesses that are in industries as healthcare, finance, or government contracting. A compliance or regulatory obligation may have strict requirements regarding data protection and how records are to be kept or reported. Laptop monitoring is a way of assuring businesses that they comply with regulations under which they are regulated (e.g., HIPAA, SOX, PCI-DSS, GDPR) by keeping a record of their employees access points by way of maintaining an audit trail/history of employee actions — regarding content access, the ability for reports to automatically be generated, and via usage of a monitoring system for employee activity.
Finally, although asset management isn’t the main reason for these laptop monitoring implementations, the fact that many organizations have very large fleets of organization-issued devices plays a governing role in the decision to implement laptop monitoring. Monitoring software can monitor how employees use devices, ensure the intended level of activity for software installations, and ascertain that it is being used for the intended purpose of resources.
This can also extend to blocking unauthorized software download activity, bandwidth usage, and identifying the actual physical locations of mobile devices. Companies can use laptop monitoring data to maximize IT investments, identify unused software licenses, and protect company resources from being used for personal activities.
Key Laptop Monitoring Tool Features
Modern laptop monitoring tools provide comprehensive activity tracking in real-time, with the ability to see employee behavior and patterns almost instantly. The modern monitoring platform continuously monitors active applications, recording mouse and keyboard movement, and measuring idle time to create a timeline of activity. With real-time dashboards, managers can see the monitoring platform’s current employee status, which applications are in use, the websites visited, and the overall productivity score. This allows managers to intervene when needed, and employees are made aware of their work-related activity patterns.
Automated screenshots are one of the key features of laptop monitoring tools, enabling periodic images of the employee’s screen to be captured at pre-scheduled periods. During setup, screenshots can also be configured to initiate the task when a specific trigger occurs, such as visiting a site, opening an application, or unusual activity patterns. There are also advanced screenshot properties such as auto-blurring sensitive data, taking screenshots of certain application types, and image intelligence to capture and flag potentially problematic content.
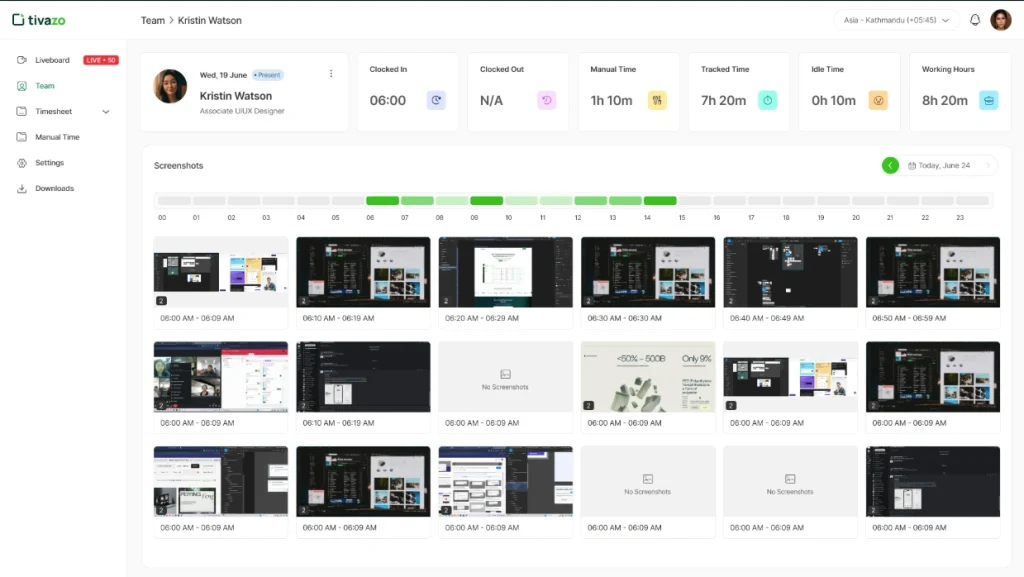
This feature is completely automated, which means that there is automatic monitoring that does not require supervisor involvement.
Website and application usage logs provide insights about digital behaviors by capturing all the particulars of what sites employees visited, how long they were on each platform, and whether those things are considered productive or non-productive. Employee logs can show the most popular applications used, reveal patterns in their internet surfing habits, and show possible security risks of going to bad sites (e.g., phishing attempts). More advanced usage logging categorizes activity, assigns a productivity score according to types of apps used, and provides trend analysis that shows how usage changes over time.
Alerting and behavior analytics capabilities will allow for proactive monitoring of employees, in that they will automatically alert supervisors/administrators when specified conditions are met. When intelligently detecting unusual behaviors or patterns, automated systems can alert administrators to issues like an unusual login time, lots of personal website activity, three attempts to visit the same random restricted material, etc. Employee behavior analytics use machine learning algorithms to create baseline patterns of employees and will alert when their activities differ significantly from normal patterns. Organizations can set specific thresholds and criteria for alerts according to their unique sectors of productivity and security.
Cloud-based dashboards collate the laptop monitoring data and display the information in accessible and user-friendly interfaces that provide overall monitoring capabilities.
These platforms can provide role-based access controls, providing reasonable levels of security accordingly to the type of stakeholder with access to the information. They also provide robust reporting capabilities that automatically provide summaries, trends in productivity, reviews of security incidents, and so forth, that will assist organizations in using the data collected to assess best practice management regarding workforce planning and security protocols.
Legal & Ethical Considerations
- Applying ethical practices with employee laptop monitoring hinges upon the element of transparency with employees. Therefore, organizations should transparently communicate their monitoring practices, purposes, and extent before the implementation of monitoring. Companies should provide full explanations of the employee laptop monitoring practices to employees. Companies should provide sufficient details on what activities will be monitored, how the information will be used, and who will have access to the data collected.
- Transparency will sometimes take commitment beyond the point of simply communicating monitoring practices to employees. Companies should also timely communicate how monitoring data is being used, what conclusions were derived from the data, and how the information is working to make conditions better at work. A methodical ongoing communication process will help build trust between employers and employees; employee laptop monitoring is used for legitimate business processes that improve workplace conditions rather than an intrusive process of surveillance.
- Laptop monitoring implementation is greatly affected by employee data protection regulations. There are, of course, various laws in place, like GDPR, HIPAA, and a number of state privacy laws that place strict restrictions on the surveilling of employees, as well as regulations for business use of employee data. Each has specific consent requirements, data retention requirements, and municipal countries with specific rights regarding one’s privacy and information collected via monitoring technology. Regardless of compliance, organizations need to give consideration to any applicable privacy laws when establishing employee laptop monitoring, but also give due regard to the employee’s rights to access their monitoring data, request corrections, and understand the extent of processing regarding their collected information.
- For organizations with global operations, there is also the involvement of additional considerations, as there are laws that vary across every jurisdiction, as well as employee rights that vary by voluntary law and helpful or jurisdictional state laws. Presumably, organizations engaged in laptop monitoring across jurisdictions are implementing similar staff monitoring standards and will have region-specific policies that can be modified to suit the particular jurisdiction. As employee data protection regulations are growing and changing, compliance should be reviewed regularly by an organization’s legal representatives.
- However, agreements regarding consent and company policies need to balance legal convenience with employee rights, general rights, and the provisions of other laws, to develop positive employer/employee relationships, allow for the duty of fairness when deciding issues affecting employees at work, and avoid and minimize harm. Good or effective consent not only has more elaborate consent forms depending on the local laws and cultural boundaries, but also includes educational strategies and protocols for informing employees about monitoring practices and the purposes of that monitoring, describing in detail how the employee’s data are or will be collected in the monitoring process, and informing them of any options to opt out of monitoring, when that is lawful.
- Company policies must attempt to balance legitimate business needs and employee privacy expectations, which are two different things, and set reasonable limits on monitoring behaviors and provide employees the ability to raise concerns or issues regarding their laptop monitoring practices.
Laptop Monitoring in Remote & Hybrid Work
One of the pitfalls of working through a pandemic was seeing the escalation of remote and hybrid working models, and with it, the associated reliance on and importance of laptop monitoring. As organizations sought options to work remotely, they lost visibility and control over dispersed workforces and therefore became reliant on employing laptop monitoring as a way to manage their remote workforce.
Managing a remote workforce is inherently more complex and challenging than managing an in-office employee. The concept of managing remote employees using the same techniques and approaches that you would use in an office or a physical work environment is simply not appropriate and ultimately ineffective.
Thus, the need to continue to use laptop monitoring as a tool to support employee productivity, compliance, security, and accountability. Companies employing remote work policies are going to rely heavily on monitoring systems to, at minimum, maintain an appropriate level of oversight on operations, but to understand what employees are doing in a project and ensure that employees are engaged even though they don’t see and interact with them in a traditional office space.

Statistically speaking, the impact of laptop monitoring is significant. Studies indicate that organizations using a comprehensive employee monitoring system documented 23% more productivity than those that did not use monitoring software to support remote work employees. Companies with laptop monitoring systems reported 40% fewer security incidents with remote workers compared to those without monitoring capabilities and had 35% better tracking of project deadlines. These statistics indicate how monitoring software helps mitigate issues of managing a dispersed workforce while providing a measurable business benefit.
The case examples provided demonstrate some of the practical uses of monitoring laptops in remote environments. For example, a technology consulting firm, by deploying monitoring of laptops, was able to more accurately track billable hours and improve billing accuracy to their clients by 15%, and improve project profitability. A financial service company leveraged the laptop monitoring data to examine if there were remote employees struggling with the implementation of new software and built targeted training interventions to fix the issues. In healthcare organizations, they use monitoring of laptops to ensure compliance with HIPAA laws, with remote workers accessing patient medical records while remote work was allowed.
Monitoring of laptops not only enables more effective management of remote workforces for productivity tracking, but it also provides additional information related to communication and collaboration. For instance, the monitoring can determine communication habits, usage of collaboration tools, and possible isolation among remote team members. Using the monitoring data, managers and team leads can not only provide better support for their team members but also help to optimize team structures and experiences to ensure remote staff still feel connected to their team and organizational culture.
Some of the challenges to monitoring remote laptops include: employee concerns with privacy, the technical challenges that may arise from implementing monitoring, and cybersecurity risks.
Organizations face challenges that must be met with explicit policies, reliable monitoring systems, and ongoing communications with their remote workforce. Ways to solve the challenge of productivity and security are privacy-centric monitoring protocols, monitoring data through secure VPN channels, and duties involving work and personal devices should be explicit. Any remote monitoring program involves balancing the need to monitor workers with their emotional need for autonomy and trust, while ensuring sufficient measures are in place for business purposes, viability, and control.
Selecting Laptop Monitoring Software
There are many criteria to analyze when choosing appropriate laptop monitoring software; however, these should be considered from the perspective of the organization’s needs, technical requirements, and compliance obligations. Usability is first and foremost; the monitoring system should be easy to use for both the IT administrator and the end users, and should not require extensive technical training.
Usability can include user interface design, ease of navigating the monitoring dashboard, and the extent of configuration, which will ensure successful implementation and continued use and management of the laptop monitoring program. Organizations should trial the practicalities of software usability through first-hand pilot programs and consultation sessions with users. These practical user testing sessions should be included in your analysis of any software solution your organization is choosing.
Scalability is a vital consideration for growing organizations. Laptop monitoring solutions will be expected to scale capacity and be able to manage more users, devices, and data without degradation of the systems’ performance. Scalable solutions offer scalable licensing, cloud-based architecture that can be scaled up as needed, and provide infrastructure that has the capability of offering a professional services-enhanced monitoring solution if needed. Organizations will want to think about the anticipated growth and determine if they have any laptop monitoring tools that can scale up with the organizational growth to adapt to changing organizational needs without requiring complete replacement of the entire system.

Another consideration for organizations is compliance options as part of meeting regulatory requirements. Organizations will want to examine how well the monitoring solution meets compliance with organizational regulations when reviewing compliance requirements. Good compliance attributes will be the ability to produce an automated audit trail for monitoring storage data retention, data storage needs to be secured, and a reporting mechanism that allows for regulatory reporting types to prove compliance. Organizations will want to determine if the laptop monitoring software meets compliance certification requirements and can produce documentation for regulatory audits.
Some of the top products for monitoring employee laptops are Tivazo’s productivity and compliance solution, specifically for enterprise structures. Clockify is a project-based organization with monitoring capabilities. Teramind has strong behavior analytics and insider threat capabilities with a clear security focus. If you are looking for a productivity-based solution for your team, DeskTime is an option. Hubstaff is a productivity-based remote team management solution, and ActivTrak secured strong resource-dedicated activity analytics. Each of the options above is viable, with its value propositions, and organizations will evaluate the value of these propositions differently.
Be mindful of how your monitoring solution will be accommodated by the existing IT infrastructure and business applications. It is in the organization’s best interest to understand this so that deployment and continued operation is executed seamlessly. Organizations should also consider how the monitoring solution integrates with the other tools used in technology tools such as HR systems, security solutions, or productivity tools, so that they establish an integrated technology ecosystem to realize additional benefits from their monitoring investment.
Final Remarks
The point has transitioned from merely monitoring employees’ laptop use to a real-time monitoring tool that delivers organizational intelligence through a lens that explores workforce productivity, organizational security, and operational efficiency. The ethical framework of developing a workflow laptop monitoring culture can provide organizations with the chance to engage productively, protect organizational data, and maintain regulatory compliance, while allowing employers to respect employee privacy and maintain and build positive organizational relationships.
In business value, Monday by is much more than just recording the level of employee activity; in fact, it adds the potential for true workforce analytics to support the informed decision-making process. Organizations that are thoughtful about monitoring report overall organizational productivity, restore security triggers before security incidents, and adhere to mandated compliance. The data indicates that with ethical monitoring implementation, transparency and ethical monitoring can be powerful for organizations in a complex and rapidly changing workplace.
The evolution of work and remote work as part of the organizational model also highlights the importance of the evolving influence of monitoring on workforce development going forward. Organizations that can properly consider the organizational legal framework, potential ethical implications, and technology to enable effective monitoring will find themselves in the best possible position to realize the full benefits of valuable and current monitoring technologies while maintaining employee trust and engagement.
If you are considering learning about laptop monitoring to see if it could support your organization, you can take the next steps and review top-rated monitoring solutions that align with your specific organizational goals and compliance needs. You may want to include a pilot program to experience both the impact of monitoring on your employee productivity and security posture as well as your organization, which would be the way the risk posture changes relative to compliance.
Contact reputable vendors such as Tivazo, Teramind, or recommended monitoring solutions for the demonstrations and discuss the potential implementation based on meeting your organizational goals. Your investment in an end-to-end laptop monitoring capability will provide returns on investment multiple times over, in terms of operational visibility, security protection, and actionable intelligence to support improvements in your business outcomes.




